WolfPack Overview¶
Wolfpack is the codename for a deployable cluster or Pack of Network Fuction Virtualization (NFV) security appliances. This pack provides IPS, Firewall and Segment Routing functionality. Currently Wolfpack is only deployed at the Edge on ANGEL with the plan to bring security services to other enclaves in the future.
High Level Design for ANGEL Edge¶
The following diagram provides the current layout of the VMware Virtual Switches, Portgroups and the associated Virtual machines and ports on the secuirty appliances.
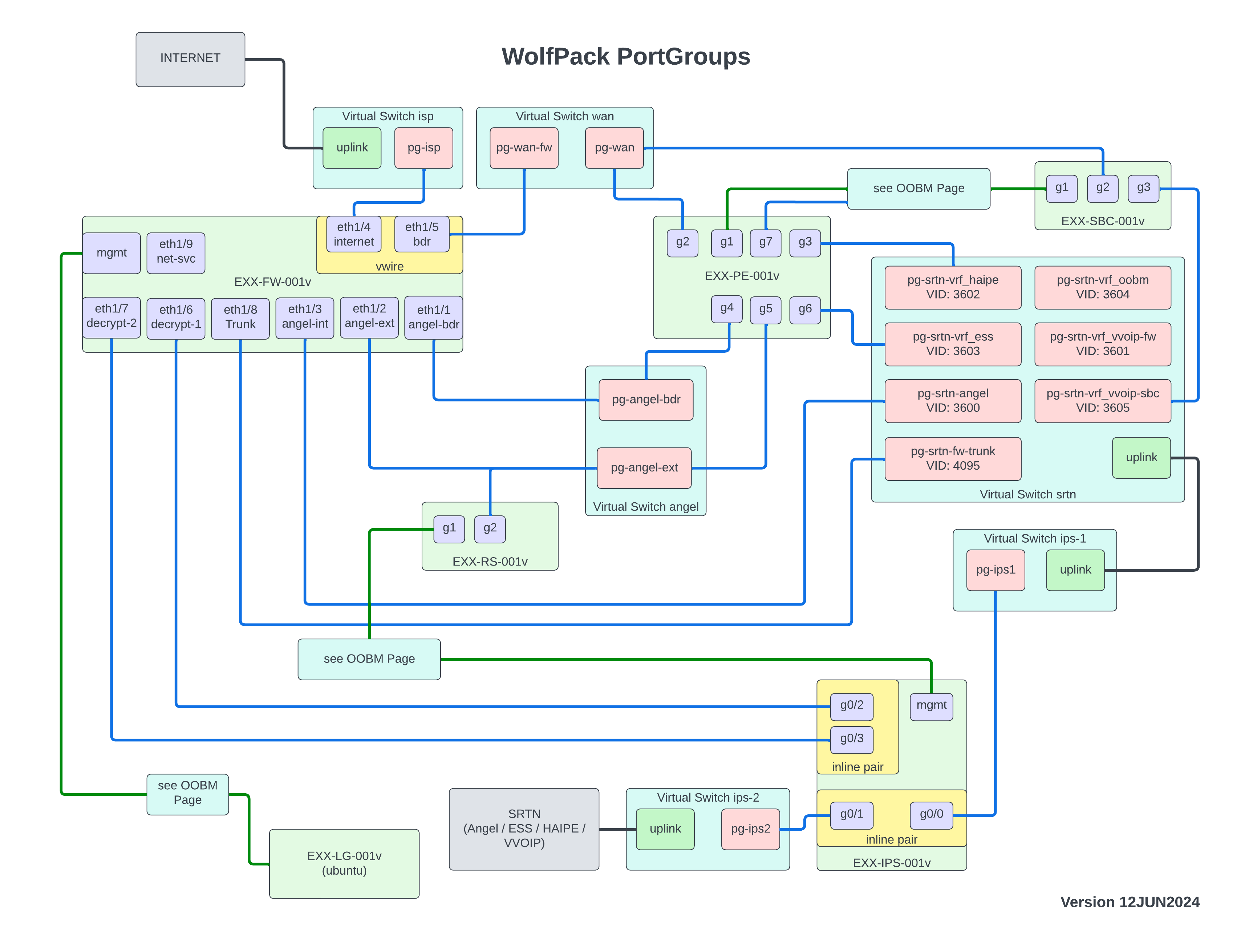
In Figure 1 above there are 7 vSwitches that required for the deployment WolfPack
Swicthes and Port Groups
-
isp: This vSwitch is responsible for providing access to the physical interface that corresponds to PCIe Slot 1 Port 1 on the Cisco UCS C240-M6, as well as connectivity to the Palo Alto Virtual Firewall's border virtual-wire for the network's border.
- pg-isp: This port group requires the following security policy to ensure that traffic flows through the virtual-wire.
- Promiscuous mode: Accept
- MAC address changes: Accept
- Forged Transmits: Accept
- pg-isp: This port group requires the following security policy to ensure that traffic flows through the virtual-wire.
-
wan: This vSwitch connects to the Palo Alto Virtual Firewall's border virtual-wire and provides a globally routable IPv4 Address to the site's Provider Edge (PE) and Session Border Controller (SBC). The wan vSwitch has the following associated port groups:
- pg-wan-fw: This port group requires the following security policy to ensure that traffic flows through the virtual-wire.
- Promiscuous mode: Accept
- MAC address changes: Accept
- Forged Transmits: Accept
- pg-wan: This port group is used to connect services that require a globally routable IPv4 Address. In the basline deployemnt this port group is used by the PE and SBC on interface g2 in the internet vrf.
- pg-wan-fw: This port group requires the following security policy to ensure that traffic flows through the virtual-wire.
-
angel: This vSwitch provides connectivity between the PE, FW, and Route Server (RS) and has the following associated port groups:
- pg-angel-bdr: This connects the PEs' interface GigabitEthernet4 (internet vrf) to the FWs' angel-bdr zone on Ethernet1/1.
- pg-angel-ext: This is used for connectivity to the PE on interface GigabitEthernet5 (angel vrf) which provides a MPLS L3VPN service allowing intersite ANGEL communication. In addition the RS is in this subnet.
-
srtn: This switch is used to connect HAIPE, ESS, VVOIP, OOBM, ANGEL and other service to the Segment Routing Transport Network (SRTN). This switch has a uplink that comes back into the servers ips-1 vSwitch. This vSwitch has the following associated port groups:
- pg-srtn-angel: This port group has a VLAN Tag of 3600 and connects the FWs' angel-int zone to the physical network through the DC-SVC switch stack.
- pg-srtn-vrf_pe: This port group has a VLAN Tag of 3602 and connects the PEs' interface GigabitEthernet3 to the DC-SVC switch stack which allows TACLANES to connect to the HAIPE MPLS L3VPN for intersite HAIPE connections.
- pg-srtn-vrf_ess: This port group has a VLAN Tag of 3603 and connects the PEs' interface GigabitEthernet6 to the DC-SVC switch stack which allows ESS to connect to the ESS MPLS L3VPN for intersite ESS connections.